Learn
Zero-knowledge proofs on Stellar
Imagine living in a world where trust, privacy, and efficiency coexist seamlessly. Zero-knowledge proofs (ZK Proofs) make this possible, ensuring that privacy, scalability, and interoperability go hand in hand.

By leveraging ZK Proofs on the Stellar Network, we can increase privacy for unbanked people across the globe, enhance scalability for cross-border payment systems, and interoperability for cash-to-crypt applications. This guide will help you understand the basics, applications, and significance of ZK Proofs in today's digital landscape.
What are zero-knowledge proofs?
ZK Proofs are a breakthrough in cryptographic technology. They allow one party to prove to another that a statement is true without revealing any information beyond the validity of the statement itself.
While it might sound like a simple concept, the underlying method of Zero-Knowledge Proofs is truly a landmark mathematics achievement. This technology has been researched for over four decades, first introduced in 1985 in the paper "The Knowledge Complexity of Interactive Proof-systems" [GMR85]. The development of various types of proofs, such as SNARK and STARK, which came later, has been particularly crucial in blockchains, demonstrating the depth and utility of this groundbreaking work.
How do zero-knowledge proofs work?
In ZK Proof systems, the goal is simple: a prover seeks to convince a verifier that a statement is true without revealing other information.
For example, on the Stellar network, a verifier could ensure that the prover’s wallet contains more than X USDC without knowing the exact amount.
Key Concepts of ZK Proofs:
Completeness
If the statement is true, then a prover can convince a verifier.
Soundness
A cheating prover can not convince a verifier of a false statement.
Zero-Knowledge
Only the statement's truth is revealed, nothing else.
Scalability
ZK Rollups are a scaling solution aggregating multiple transactions into a single proof to be verified on the blockchain, increasing throughput and reducing transaction costs.
Benefits
Zero-knowledge proofs on Stellar
Regarding network performance, Stellar aims to surpass other networks by utilizing the full capabilities of modern computing and executing disk, CPU, and network operations simultaneously. By placing these cryptographic processes into dedicated “slots” within each block, the Stellar core protocol can handle larger volumes of transactions without slowing down or putting extra strain on its infrastructure.
Let’s have a look at a block's resource allocation.
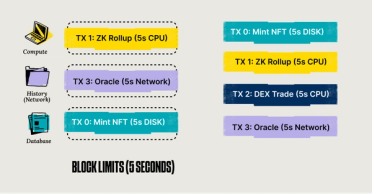
The transactions (txs) on the right are a pool of txs submitted to the network. On the left is the block that will be applied and added to the blockchain—the more txs in a block, the higher the TPS. By having a separate lane or "slot" in the block per resource type, in this case, for a ZK Proof operation, we can fit up to 3x more txs per block (which means up to 3x TPS). This approach is beneficial for validators and operators, especially when handling large volumes of transactions, as it alleviates the typical computational burden seen with other fee models.
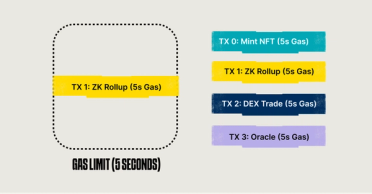
For example, a single resource gas fee approach:
Applications of ZK proofs
- Identity/Data Ownership in Social Networks of Web3: In decentralized social networks, ZK Proofs can verify user identities and data ownership without exposing personal information. Users can prove they are eligible to access certain services or content without revealing their identity, thus maintaining privacy and control over their data.
- Decentralized Finance (DeFi): In DeFi applications, ZK Proofs can provide functionality to enhance the privacy and security of financial transactions. For example, users can prove ownership of assets or the ability to repay a loan without revealing their entire portfolio.
- Access to Financial Services: Microfinance institutions can use ZK Proofs to verify individuals' creditworthiness without delving into their financial history. This can help unbanked individuals obtain loans, insurance, and savings accounts, providing opportunities to improve their economic status.
- Privacy-Preserving Financial Inclusion Programs: NGOs can use ZK Proofs to implement financial inclusion programs that protect beneficiaries' privacy. For instance, cash transfer programs can verify eligibility and distribute funds without publicly revealing recipients' personal data. This ensures that aid reaches those in need without exposing them to potential social stigma or targeting.
Implementations and Technologies
Zk-SNARKs (zero-knowledge succinct non-interactive argument of knowledge)
SNARKs are a type of cryptographic proof that allows one party to prove to another that they know a value without revealing the value itself and without any interaction between the prover and the verifier after the proof has been generated. These proofs are succinct, meaning they are very small and quick to verify, which makes them highly efficient. zk-SNARKs are widely used in privacy-preserving applications to enable transactions where the details remain confidential while ensuring the transaction's validity.
Applications of zk-SNARKs:
- Verifiable computation: zk-SNARKs facilitate outsourcing expensive computations and validating the correctness of the results without redoing the execution. This model shifts the blockchain paradigm from everyone computing the same to one-party computing and everyone verifying.
- Decentralized applications (Dapps): ZK-SNARKs can be used in Dapps to enable privacy-preserving smart contracts and off-chain computations. For instance, a Dapp could use ZK-SNARKs to confirm a user’s eligibility for a service without revealing their personal information.
- Privacy-preserving payments: zk-SNARKs enable fully anonymous transactions, keeping the amounts and the parties involved completely private. For example, they allow for payments without attaching any identity, ensuring complete anonymity. One use case may be funding a public goods campaign without exposing a user’s identity.
Implementations and Technologies
Zk-STARKs (zero-knowledge scalable transparent arguments of knowledge):
STARKs are an advanced form of cryptographic proof that enhances scalability and transparency. They are designed to minimize the interaction between the prover and the verifier, significantly speeding up the verification process compared to zk-SNARKs. These proofs are well-suited for applications requiring high throughput and scalability, such as large-scale blockchain systems and intensive privacy-preserving computations.
Applications of zk-STARKs:
- Scalable blockchain systems: The proofs are bigger. However, ZK-STARKs are designed to handle large amounts of data and complex computations efficiently. It's like having a more detailed receipt that takes longer to read but can prove more complex transactions.
- Verifiable computation: Similar to zk-SNARKs, zk-STARKs facilitate verifiable computation, allowing untrusted parties to perform computations while providing cryptographic proof of correctness. This ensures that computations can be trusted without revealing the underlying data.
- Privacy-preserving data analysis: zk-STARKs can be used in privacy-preserving data analysis scenarios, where sensitive data can be processed without revealing the underlying data. For example, they can be used to verify large sets of health data without revealing the underlying patient information.
Challenges and considerations
Computational Complexity: Implementing ZK Proofs requires significant processing power, but Stellar's infrastructure optimizes resources to handle multiple operations simultaneously. By utilizing multi-threading and parallel processing, Stellar optimizes using validator computing resources to handle multiple operations simultaneously. However, adding ZK Proof operations like Rollups to the Stellarstack may introduce unknown computational loads on the network, requiring careful monitoring and optimization to ensure sustained network performance.
Trust Assumptions: The security of ZK Proof systems relies on specific cryptographic assumptions that must be rigorously tested and validated. For example, implementing functions for advanced cryptographic curves is crucial for sophisticated cryptographic operations in the Stellar ecosystem. This includes functions like elliptic curve point addition and multiplication. However, essential components such as pairing operations and hashing to the curve still need to be implemented in the Stellar core protocol to ensure full functionality.
Illicit Finance Mitigations: Employing ZK Proofs for on-chain privacy solutions can present legal challenges. Regulators and law enforcement around the world have been cracking down on mixers and privacy wallets lacking robust illicit finance controls. The blockchain industry is working hard to develop strategies and alternatives that can satisfy privacy and compliance concerns.The Stellar Development Foundation is collaborating with industry partners and technical and compliance experts to advance the adoption of compliant privacy designs.
Join the discussion
Stellar is actively working on integrating ZK operations into the Stellar network. Join the community to help shape Stellar’s capabilities! Visit the GitHub discussion on ZK implementation.